Who doesn’t love the smell of fresh new IP addresses? Well, anyone charged with warming IP addresses for...
Why do you need to verify an email address?
As the mailbox providers get tighter and tighter about what email they will deliver, the importance of a clean email list increases. How does one get a clean email list? The answer is email verification. Before you add anyone to your email list, you should check that email address with an email verification service. AudiencePoint’s verification service takes email addresses through a series of sanity checks and arrives at the following conclusions based on our second party data pool:
Possible email verification responses
| Engaged | The email address exists and is known to engage with emails frequently. |
| Disengaged | The email address exists, but is inactive. |
| Verified | The email address exists. |
| Invalid | The email address is syntactically invalid, i.e. it contains a common domain spelling mistake, does not accept incoming mail, or is known to not exist. |
| Spamtrap | The email address is a known spam trap. |
| Role | The email address is a role based email address (e.g., admin, postmaster, team, ect.) |
| Caution | The email address is a valid email address, but we recommend against emailing it in most cases. |
| Unknown | The email address is in valid format, but we are unable to verify that it exists. |
Choose what you are comfortable with
Because there are so many return values, you can identify which conditions you are comfortable with including in your email database.
How is our verification endpoint better?
The email verification endpoint returns the same hygiene values that every other verification provider returns with the addition of a measure that also identifies how engaged a given email address is within our second-party data pool.
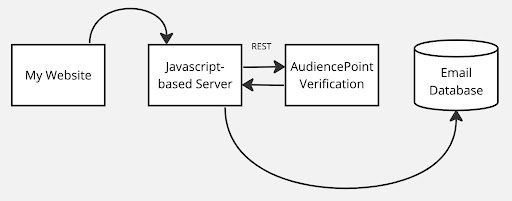
How does it work?
You make a single REST call per email address. REST stands for Representational State Transfer. REST uses the same https protocol that web pages use, except you are returned information versus a webpage (html).
You’ll need a server
I know that sounds like a big deal, but f you are cleaning the email at the point of collection then you already have a server! The server is where the verification code runs.
Can I run the verification from the browser?
So technically yes, but your browser will give the person who is viewing your website full access to all of the verification code, including your password. That matters because that person can then make the same verification calls from their own environment creating a situation where you have to pay for their verification service.
What technology should I use?
That depends on your hosting environment. The most common hosting environment is Javascript hosted through Node.js. AudiencePoint has created an SDK for Node.js javascript users.
Keep it safe
Remember that your customer key for email verification needs to stay protected therefore it needs to run on the server and not within the browser.
The codes
Once your environment is setup, the Javascript code to verify is easy to setup:
const email = "<EMAIL_ADDRESS>"; // The email address you want to validate
verificationAPI.verifyEmail(email)
.then(res => {
console.log(res.Email);
console.log(res.Result);
if (res.Suggestion != null)
console.log(res.Suggestion);
})
.catch(error => {
console.log(error.message);
console.log(error.status);
});
Stuck?
Check out our developer docs, and reach out for help at our support email
support@audiencepoint.com
Now what?
Once your codes are set up, the rest is up to you. How will you handle role-based emails? Should the be included or dropped?
Conclusion
Email verification technology has been a stalwart in the email industry. It has protected email databases from problematic emails for a very long time. The AudiencePoint email verification endpoint maintains the existing hygiene paradigm while innovating with our second-party data pool to introduce additional fidelity around patterns of engagement.